The copy-protection scheme for STEM is based on the concept
of establishing the appropriate authorisation in order to run a model. To
fully understand the impact and power of D-STEM, it is helpful to compare the
authorisation strategies used for conventional and run-time models. The term model
engine is used in the following sections to refer to the software component
which is used to run a model and to generate the corresponding results.
Conventional authorisation
The C-STEM model engine always looks for authorisation when
a model is run, so only licensed STEM users can run a conventional model, and
only with a dongle.

Figure 1: Conventional model engine requires a
dongle
Distributable authorisation
The D-STEM Editor has an additional facility which enables a
licensed D-STEM user to ‘freeze’ the structure of a conventional model into an
exported binary run-time model file. This process is authorised by the
presence of a D-STEM dongle, and this authority is ‘stamped’ into the run-time
model at export time. It is this digital stamp which identifies the model as a
run-time model, and which authorises it to be re-run subsequently without a
dongle, subject to limited modifications.
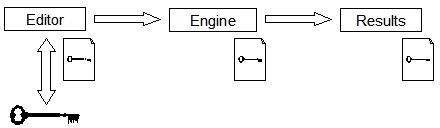
Figure 2: Distributable authorisation in run-time
model
The scope of allowed modifications is selected by the D-STEM
user at export time, but never extends to creating, renaming or deleting
elements: the structure of a run-time model is fixed. Subject to these
constraints, any STEM Editor can be used to modify input assumptions without
compromising the run-time status of the model.